February/2023 Latest Braindump2go 350-601 Exam Dumps with PDF and VCE Free Updated Today! Following are some new Braindump2go 350-601 Real Exam Questions!
QUESTION 236
An engineer configured an environment that contains the vPCand non-vPC switches, however, it was noticed that the downstream non-vPC switches do not receives the same STP bridge ID from the upstream which vPC feature must be implemented to ensure must be implemented to ensure that vPC and non-vPC switches receive the same STP bridge ID from the upstream vPC switch peers?
A. peer-switch
B. peer-gateway
C. systam-mac 0123.4567.89ab
D. vpc local role-priority 4000
Answer: A
Explanation:
Peer switch allows the sahring of the same BPDU.
https://www.cisco.com/c/en/us/td/docs/switches/datacenter/nexus9000/sw/6-x/interfaces/configuration/guide/b_Cisco_Nexus_9000_Series_NX-OS_Interfaces_Configuration_Guide/b_Cisco_Nexus_9000_Series_NX-OS_Interfaces_Configuration_Guide_chapter_0111.html
QUESTION 237
A network engineer must perform a backup and restore of the Cisco Nexus 5000 Series Switch configuration. The backup must be made to an external backup server. The only protocol permitted between the Cisco Nexus switch and the backup server is UDP. The backup must be used when the current working configuration of the switch gets corrupted.
Which set of steps must be taken to meet these requirements?
A. 1. Perform a startup-config backup to an FTP server
2. Copy startup-config in the boot flash to the running-config file
B. 1. Perform a running-config backup to an SFTP server
2. Copy backup-config from the SFTP server to the running-config file
C. 1. Perform a running-config backup to an SCP server
2. Copy running-config in the boot flash to the running-config file
D. 1. Perform a startup-config backup to a TFTP server
2. Copy backup-config from the backup server to the running-config file
Answer: D
Explanation:
Of the answer choices given, only TFTP uses UDP. SFTP runs on TCP 22 (but can be assigned whatever port you want, but only TCP). TFTP runs on UDP port 69. SCP runs on TCP port 22.
FTP runs on TCP port 21 to establish connection and TCP 20 to transfer data.
QUESTION 238
Refer to the exhibit. A network engineer requires remote access via SSH to a Cisco MDS 9000 Series Switch. The solution must support secure access using the local user database when the RADIUS servers are unreachable from the switches. Which command meets these requirements?
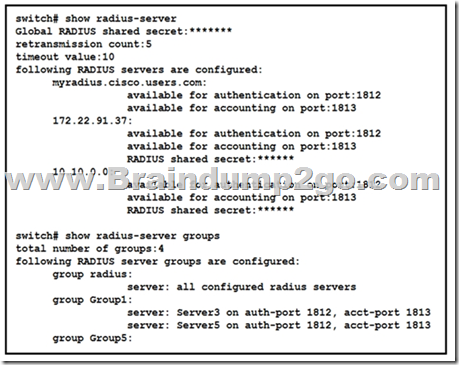
A. aaa authentication none
B. aaa authentication login default group radius
C. aaa authentication login default fallback error local
D. aaa authentication login default group local
Answer: C
Explanation:
https://www.cisco.com/c/en/us/td/docs/switches/datacenter/nexus9000/sw/6-x/security/configuration/guide/b_Cisco_Nexus_9000_Series_NX-OS_Security_Configuration_Guide/b_Cisco_Nexus_9000_Series_NX- OS_Security_Configuration_Guide_chapter_0111.html
QUESTION 240
A network engineer configures a converged network adapter (CNA) and must associate a virtual Fibre Channel 7 interface to VSAN 7. The CNA is connected to the interface Eth1/7, and VLAN 700 is mapped to the VSAN. Which configuration must be applied to create the virtual Fibre Channel interface and associate it with the Ethernet physical interface?
A. switch(config)# vlan 700
switch(config-vlan)# fcoe vsan 7
B. switch(config)# vsan database
switch(config-vsan)# vsan 7 interface vfc 7
C. switch(config)# interface ethernet 1/7
switch(config-if)# vfc 7 attach vlan 1,700
D. switch(config)# interface vfc 7
switch(config-if)# bind interface ethernet 1/7
Answer: D
Explanation:
https://www.cisco.com/c/en/us/td/docs/switches/datacenter/nexus5000/sw/fcoe/421_n1_1/b_Cisco_n5k_fcoe_config_gd_re_421_n1_1/Cisco_n5k_fcoe_config_gd_re_421_n1_1_chapter4.html
QUESTION 241
An engineer must use the Embedded Event Manager to monitor events that occur on a cisco Nexus 9000 series switch.
An environment variable needs to be created so that several policies use the monitored events in in their actions.
The external email server is represented by IP address 10.10.10.10.
Which command sets the environment variable?
A. N9k2(config)# event manager policy environment mallserver `’10.10.10.10”
B. N9k2# event manager environment mallserver `’10.10.10.10”
C. N9k2 (config-apple1)# environment mallserver `’10.10.10.10”
D. N9k2 (config)# event manager environment mallserver `’10.10.10.10”
Answer: D
Explanation:
To set an Embedded Event Manager (EEM) environment variable, use the event manager environment command in global configuration mode.
Reference:
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/eem/command/eem-cr-book/eem-cr-e1.html
QUESTION 242
Which communication method does NFS use for requests between servers and clients?
A. XDR
B. SSC
C. RPC
D. SMB
Answer: C
Explanation:
The Network File System (NFS) is an application where the user can view, store and update the files on a remote device. NFS allows the user to mount all or a part of a file system on a server. NFS uses Remote Procedure Calls (RPC) to route requests between the users and servers.
Reference:
https://www.cisco.com/c/en/us/td/docs/routers/nfvis/config/3-7-1/nfvis-config-guide-3-7-1/nfvis-config-guide_chapter_01100.html
QUESTION 243
A customer reports Fibre Channel login requests to a cisco MDS 9000 series Switch from an unauthorized source.
The customer requires a feature that will allow all devices already logged in and learned in and learned to be added to the Fibre channel active database.
Which two features must be enabled to accomplish this goal? (Choose two.)
A. Auto-learning
B. Port security
C. Enhanced zoning
D. Device aliases
E. Smart aliases
Answer: AB
Explanation:
Port Security Activation
By default, the port security feature is not activated in any switch in the Cisco MDS 9000 Family.
By activating the port security feature, the following apply:
Auto-learning is also automatically enabled, which means:
From this point, auto-learning happens for the devices or interfaces that were already logged into the switch and also for the new devices will login in future.
You cannot activate the database until you disable auto-learning.
All the devices that are already logged in are learned and are added to the active database.
All entries in the configured database are copied to the active database.
After the database is activated, subsequent device login is subject to the activated port bound WWN pairs, excluding the auto-learned entries. You must disable auto-learning before the auto-learned entries become activated.
https://www.cisco.com/en/US/docs/storage/san_switches/mds9000/sw/rel_3_x/configuration/guides/fm_3_3_1/psec.html
QUESTION 244
An engineer evaluates a UI-based infrastructure management system capable of monitoring and deploying standalone VXLAN BGP EVPN deployments. The storage administrators also need the solution to manage the Cisco MDS 9000 Series Switches. Which solution meets these requirements?
A. Cisco Intersight
B. Cisco UCSD
C. Cisco Tetration
D. Cisco DCNM
Answer: D
Explanation:
Cisco Nexus Dashboard Fabric Controller (NDFC) (formerly DCNM) is the network management platform for all NX-OS enabled deployments. It spans new fabric architectures, storage network deployments, and IP Fabric for Media.
Reference:
https://www.cisco.com/c/en/us/products/cloud-systems-management/prime-data-center-network-manager/index.html
QUESTION 245
Refer to the exhibit. Which backup operation type not include the preserve identities feature?
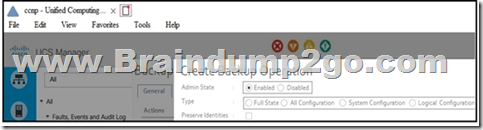
A. Full state
B. Logical configuration
C. System configuration
D. All configuration
Answer: A
Explanation:
Full State backup does not have Preserver Identity feature.
QUESTION 246
Refer to the exhibit. Which configuration ensure that the cisco Nexus 7000 series switches are the primary devices for LACP?
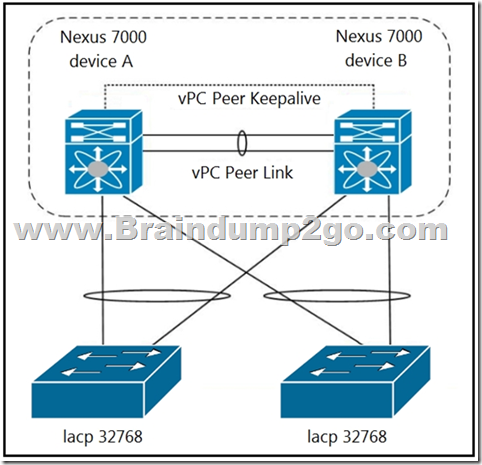
A. N7K_A(config-vpc-domain)# system-priority 4000
N7K_B(config-vpc-domain)# system-priority 4000
B. N7K_A(config-vpc-domain)# system-priority 100
N7K_B(config-vpc-domain)# system-priority 200
C. N7K_A(config-vpc-domain)# system-priority 32768
N7K_B(config-vpc-domain)# system-priority 32768
D. N7K_A(config-vpc-domain)# role priority 1
N7K_B(config-vpc-domain )# role priority 2
Answer: A
Explanation:
What is the purpose and usage of the system priority command under vpc configuration mode? The vpc quick config guide mentioned:
“You should manually configure the vPC system priority when you are running Link Aggregation Control Protocol (LACP) to help ensure that the vPC peer devices are the primary devices on LACP”.
When you manually configure the system priority, ensure that you configure the same priority value on both vPC peer devices.
If these values do not match, vPC will not come up.
QUESTION 247
A network engineer must enable port security on all Cisco MDS Series Switches in the fabric. The requirement is to avoid the extensive manual configuration of the switch ports. Which action must be taken to meet these requirements?
A. Activate CFS distribution and the auto-learning port security feature.
B. Activate CFS distribution and file auto-learning port security feature on a per-VSAN basis.
C. Enable the auto-learning port security feature on a per-VSAN basis.
D. Enable the auto-learning port security feature.
Answer: B
Explanation:
You can instruct the switch to automatically learn (auto-learn) the port security configurations over a specified period. This feature allows any switch in the Cisco MDS 9000 Family to automatically learn about devices and switches that connect to it. Use this feature when you activate the port security feature for the first time as it saves tedious manual configuration for each port. You must configure auto-learning on a per-VSAN basis. If enabled, devices and switches that are allowed to connect to the switch are automatically learned, even if you have not configured any port access.
When auto-learning is enabled, learning happens for the devices or interfaces that were already logged into the switch and the new devices or interfaces that need to be logged in. Learned entries on a port are cleaned up after you shut down that port if auto-learning is still enabled.
Reference:
https://www.cisco.com/c/en/us/td/docs/switches/datacenter/mds9000/sw/8_x/config/security/cisco_mds9000_security_config_guide_8x/configuring_port_security.html#task_1002617
QUESTION 248
A network engineer is deploying a Cisco All-Flash HyperFlex solution. Which local storage configuration is required for the operating system and persistent logging?
A. Two solid state drives
B. Two SATA drives
C. One SATA drive
D. One solid state drive
Answer: A
Explanation:
Using persistent logging allows to write logged messages to file(s) on router’s flash disk. The advantage is unlike memory buffer (DRAM) contents these files persist when the router reboots (DRAM contents are erased during a reboot.) Hence if you writing to disk it can run the OS and must wait. So 2 disks as a minimum.
QUESTION 249
An engineer configures the properties of a Cisco UCS Cisco Integrated Management Controller network adapter for a standalone Cisco C-Series Server. The Failback Timeout in the vNIC was set to 600. When the failure occurs, the secondary interfaces must be used and then failback when the primary interface becomes available again. Which action must be taken to meet these requirements?
A. Set default VLAN on the adapters.
B. Increase Cos to 6.
C. Disable VNTAG mode.
D. Enable Uplink failover.
Answer: D
Explanation:
QUESTION 250
A network engineer must prevent data comuption due to cross fabric communication in an FCoE environment. Which configuration must be applied to the Cisco Nexus Unified Switches to achieve this objective?
A. Switch(config)#fcoe fcmap 0x0efc2a
B. Switch(config-if)# no fcoe fcf-priority 0
C. Switch(config-if) # shutdown lan
D. Switch(config) # no fcoe fcf-priority
Answer: A
Explanation:
You can prevent data corruption due to cross-fabric talk by configuring an FC-Map that identifies the Fibre Channel fabric for this switch.
When the FC-Map is configured, the switch discards the MAC addresses that are not part of the current fabric.
An FCF can assign Fabric Provide MAC Addresses (FPMA) to the CNAs consisting of the FC-Map Value for the Fabric and the Fibre Channel ID (FCID) assigned during Fabric Login
switch# switchto vdc fcoe type storage
fcoe# configure terminal
fcoe(config)# fcoe fcmap 0x0efc2a
Reference:
https://www.cisco.com/c/en/us/td/docs/switches/datacenter/nexus7000/sw/fcoe/config/cisco_nexus7000_fcoe_config_guide_8x/configuring_fcoe.html
QUESTION 251
Which component is disrupted when the Cisco Integrated Management Controller is upgraded on a Cisco UCS Series Server?
A. Cisco UCS Manager
B. SAN traffic
C. KVM sessions
D. Data traffic
Answer: C
Explanation:
If you are using KVM to login to the Linux server or the EFI shell to update the firmware version of CIMC, when you run the activate command, the connection to CIMC is reset. As a result, the network connection is interrupted and the KVM window closes.
https://www.cisco.com/c/en/us/td/docs/unified_computing/ucs/c/sw/fwp/user/guide/Firmware_Upgrade_Utility/Using.html
QUESTION 252
A company is investigating different options for IT automation tools. The IT team has experience with Python programming language and scripting using a declarative language. The proposed tool should be easy to set up and should not require installing an agent on target devices. The team will also need to build custom modules based on the Python programming language to extend the tool’s functionality. Which automation tool should be used to meet these requirements?
A. Puppet
B. Ansible
C. NX-API
D. Chef
Answer: B
Explanation:
Ansible is an agentless automation that automates deployment, configuration management (maintain infrastructure consistency) and orchestration (execution of multiple applications in order). Ansible gains its popularity due to its simplicity for being agentless, efficient, requires no additional software installed on target machine, use the simple YAML and complete with reporting.
QUESTION 253
Refer to the exhibit. An engineer needs to implement streaming telemetry on a cisco MDS 9000 series switch. The requirement is for the show command data to be collected every 30 seconds and sent to receivers.
Which command must be added to the configuration meet this requirement?
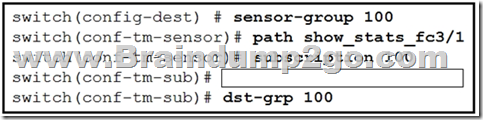
A. Sensor-grp 200 sample-period 30000
B. Snsr-grp 200 sample-interval 30
C. Sensor-grp 200 sample-period 30
D. Snsr-grp 200 sample-interval 30000
Answer: D
Explanation:
Link the sensor group with an ID to the subscription node and set the data streaming sample interval in milliseconds:
switch(conf-tm-sub)# snsr-grp id sample-interval interval
Note: The minimum streaming sample interval that is recommended is 30000.
Reference:
https://www.cisco.com/c/en/us/td/docs/switches/datacenter/mds9000/sw/8_x/config/san_analytics/cisco-mds9000-san-analytics-telemetry-streaming-config-guide-8x/configuring-san-telemetry-streaming.html
QUESTION 254
A Cisco Nexus 9000 Series Switch experiences a startup configuration corruption. The engineer must implement a procedure to recover the backup configuration file from the switch. Which command set must be used?
A. 1. Copy the running-configuration to the startup configuration.
2. Clear the current configuration of the switch.
3. Restart the device.
4. Copy a previously saved configuration file to the running configuration.
B. 1. Clear the current configuration of the switch
2. Restart the device.
3. Copy the running configuration to the startup configuration
4. Copy a previously saved configuration file to the running configuration
C. 1. Clear the current configuration of the switch
2. Restart the device.
3. Copy a previously saved configuration file to the running-configuration
4. Copy the running-configuration to the startup configuration.
D. 1. Restarting device.
2. Copy the running-configuration file to a remote server.
3. Clear the current configuration of the switch.
4. Copy the running configuration to the startup configuration
Answer: C
Explanation:
Rolling Back to a Previous Configuration
To roll back your configuration to a snapshot copy of a previously saved configuration, you need to perform the following steps:
1. Clear the current running image with the write erase command.
2. Restart the device with the reload command.
3. Copy the previously saved configuration file to the running configuration with the copy configuration-file running-configuration command.
4. Copy the running configuration to the start-up configuration with the copy running-config startup-config command.
Reference:
https://www.cisco.com/c/en/us/td/docs/switches/datacenter/nexus9000/sw/7-x/fundamentals/configuration/guide/b_Cisco_Nexus_9000_Series_NX-OS_Fundamentals_Configuration_Guide_7x/b_Cisco_Nexus_9000_Series_NX-OS_Fundamentals_Configuration_Guide_7x_chapter_01001.html
QUESTION 255
An engineer must configure OSPF in the data center. The external routes have already been redistributed OSPF. The network must meet these criteria:
– The data centre servers must reach services in the cloud and the services behind the redistributed routes.
– The exit point toward the internet should be propagated only when there is a dynamically learned default route from the upstream router.
Which feature is required?
A. Default-information originate
B. Stubby area
C. Totally stubby area
D. Default-information originate always
Answer: A
Explanation:
In OSPF, the “default-information originate” command will not advertise to any other routers without a default route in the routing table.
When added the “always” keyword, it tells the router to advertise a default route to other routers even if you don’t have a default route in the routing table.
QUESTION 256
What is a characteristic of the install all command on the cisco Nexus series switch?
A. Upgrades only certain modules
B. Automatically checks the image integrity
C. Impact data plan traffic
D. Continues the upgrade process if any step in the sequence fails
Answer: B
Explanation:
The image integrity is automatically checked by the install all command. This includes the running kickstart and system images.
https://www.cisco.com/en/US/docs/storage/san_switches/mds9000/sw/rel_1_x/1_1_1a/san-os/configuration/guide/SwImage.pdf
QUESTION 257
An engineer is using REST API calls to configure the cisco APIC. Which data structure must be used within a post message to receive a login token?
A. {“aaaUser”:{“attributes”:{“name”:”apiuser”,”pwd”:”cisco123″}}}
B. <aaaUser><name=”apiuser”/><pwd=”cisco123″/></aaaUser>
C. {aaaUser:{attributes:{name:apiuser,pwd:cisco123}}}
D. <aaaUser><name>apiuser</name><pwd>cisco123</pwd></aaaUser>
Answer: A
Explanation:
https://www.cisco.com/c/en/us/td/docs/switches/datacenter/aci/apic/sw/1-x/api/rest/b_APIC_RESTful_API_User_Guide/performing_common_tasks.html#reference_9784F9F295D14677AF3BFB98287C3ED5
QUESTION 258
The EPLD update of the supervisor module has been scheduled for several Cisco MDS 9000 Series Switches. What will be the impact of the update?
A. All control plane traffic is stopped for the duration of the EPLD update and the switch remain operational for the duration of the upgrade.
B. The redundant supervisor lakes over while the EPLD update is in progress and there is no service disruption.
C. All traffic is stopped for the duration of the EPLD update and the switch is rebooted after the upgrade is completed.
D. The redundant supervisor lakes while the EPLD update is in progress and the switch is rebooted after the upgrade is completed.
Answer: C
Explanation:
An EPLD update of the supervisor module of Fabric Switches (Cisco MDS 9100, Cisco MDS 9200, and Cisco MDS 9300 Series switches) is disruptive
since there is no redundant supervisor to take over while the update is in progress.
All traffic through the system is stopped while updating and the switch is power cycled after the upgrade has completed.
The update may take up to 30 minutes to complete.
QUESTION 259
An engineer configures an intersignt virtual application and must claim over 200 targets. The engineer starts the Claim target procedure. The engineer has prepared this initial comma- separated value file to provision the targets:
UCSFI,10.1.1.3,user-1,pwd5516b917
IMC,10.1.1.5/26,user-2,pwdc65b1c43f
HX,10.1.2.1/30,user-3,pwd39913690
UCSD,1.1.1.1.user-4,pwd5003e9d5
Which Information must be included In the comma-separated value flit to provision the targets?
A. FQON, AD name, IP address, email
B. location, address, name. password
C. certificate, user name, password. email
D. target type, hostname or P address, user name, password
Answer: D
Explanation:
For each target, add a line containing Target Type, Hostname or IP Address, User Name, and Password.
Use the CIDR notation to specify the IP Range. You can add as many lines with these details in the .csv file.
The following example shows the format to add target details in a .csv file:
https://intersight.com/help/appliance/getting_started/claim_targets
QUESTION 260
What is an advantage of NFSv4 over Fibre Channel protocol?
A. Improved security
B. Lossless throughout
C. Congestion management
D. Uses IP transport
Answer: A
Explanation:
NFS v4 includes authentication features, however this relies on external services so takes a bit more for configuration.
https://www.rcannings.com/san-storage-fc-vs-fcoe-vs-iscsi/
QUESTION 261
Which two configuration settings are available in the in the cisco UCS flmware Auto sync server policy?
A. User Notification
B. User Acknowledge
C. No Action
D. Delayed Action
E. Immediate Action
Answer: BC
Explanation:
Following are the values for the Firmware Auto Sync Server policy:
• User Acknowledge—Firmware on the server is not synchronized until the administrator acknowledges
the upgrade in the Pending Activities dialog box.
• No Action—No firmware upgrade is initiated on the server.
Reference:
https://www.cisco.com/c/en/us/td/docs/unified_computing/ucs/sw/firmware-mgmt/gui/2-2/b_GUI_Firmware_Management_22/b_GUI_Firmware_Management_22_chapter_01111.pdf
QUESTION 262
An administrator is implementing DCNM so that events are triggered when monitored traffic exceeds the configured percent utilization threshold. The requirement is to configure a maximum limit of 39913690 bytes that applies directly to the statistics collected as a ratio of the total link capacity. Which DCNM performance monitoring configuration parameter must be implemented to achieve this result?
A. Absolution Values
B. Baseline
C. Utill%
D. Per port Monitoring
Answer: A
Explanation:
You must choose either absolute value thresholds or baseline thresholds that apply to all transmit or receive traffic defined in the collection. Click the Use absolute values radio button on the last screen of the Performance Manager Configuration Wizard to configure thresholds that apply directly to the statistics gathered. These statistics, as a percent of the total link capacity, are compared to the percent utilization configured for the threshold type. If the statistics exceed either configured threshold, an event is shown on the DCNM-SAN web client Events tab.
https://www.cisco.com/c/en/us/td/docs/switches/datacenter/sw/11_x/fundamentals/cisco_dcnm_fundamentals_guide_11/monitoring_performance.html
QUESTION 263
A network architect must redesign a data center network based on OSPFv2. The network must perform fast reconvergence between directly connected switches.
Which two actions must be taken to meet the requirements? (Choose two.)
A. Configure all links on AREA 0.
B. Implement a virtual link between the switches.
C. Use OSPF point-to-point links only.
D. Set low OSPF hello and DEAD timers.
E. Enable BFD for failure detection.
Answer: CE
Explanation:
Detecting link and node failures quickly is number one priority for fast convergence. For maximum speed, relying on IGP keepalive times should be avoided whether possible and physical failure detection mechanisms should be used. This implies the use of physical point-to-point links whether possible.
BFD (BiDirectional Forwarding Detection) provides sub-second convergence for many protocols and is done in hardware. BFD will also only work on point-to- point links.
QUESTION 264
Refer to the exhibit. A host with source address 10.10.10.10 sends traffic to multicast group 239.1.1.1. How do the vPC switches forward the multicast traffic?
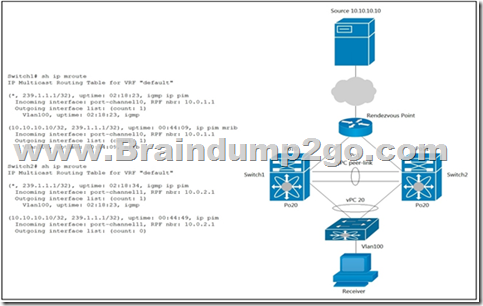
A. If multicast traffic is received on Po11 Switch2, the traffic is forwarded out only one Po20.
B. If multicast traffic is received on Po10 Switch1, the traffic is forwarded out on Po1 and Po20.
C. If multicast traffic is received on Po11 and Switch2, the traffic is dropped.
D. If multicast traffic is received on Switch over the vPC peer-link, the traffic is dropped.
Answer: C
Explanation:
Switch2 will never get the stream due to a missing OIF on Switch 2.
Reference:
https://www.cisco.com/c/en/us/support/docs/ip/multicast/214140-multicast-forwarding-in-vpc-based-on-loc.html#anc8
QUESTION 265
An engineer configured an environment that contains the vPC and non-vPC switches. However, it was noticed that the downstream non-vPC switches do not receive the same STP bridge ID from the upstream vPC switch peers. Which vPC feature must be implemented to ensure that vPC and non-vPC switches receive the same STP bridge ID from the upstream vPC switch peers?
A. System-mac 0123.4567.89ab
B. Peer-switch
C. VPC local role-priority 4000
D. Peer-gateway
Answer: B
Explanation:
The vPC peer switch is introduced to address performance concerns around these STP convergence events. This feature allows a pair of Cisco Nexus 7000 Series devices to appear as a single STP root in the Layer 2 topology. In the vPC peer switch mode, STP BPDUs are sent from both vPC peer devices. This behavior also avoids issues related to STP BPDU timeout on the downstream switches, which can cause traffic disruption. The vPC peer switch feature eliminates the need to pin the STP root to the vPC primary switch and improves vPC convergence if the vPC primary switch fails. It is important to note that the vPC peer switch is needed only when the STP root needs to be placed on the vPC pair of devices.
QUESTION 266
A company is running a pair of cisco Nexus 7706 series switches as part of a data center segment. All network engineers have restricted read-Write access to the core switches.
A network engineer must a new FCoE VLAN to allow traffic from services toward FCoE storage. Which set of actions must be taken to meet these requirements?
A. 1. Create a user-defined role and add the required privileges.
2. Assign a role to a user.
B. 1. Add the required privilege to the VDC-admin role.
2. Commit the changes to the active user database.
C. 1. Modify a network-operator role and add the required privileges.
2. Assign a VDC-operator role to a user.
D. 1. Assign the network-admin role to a user.
2. Commit the role to the switch to the active user database
Answer: A
Explanation:
User roles contain rules that define the operations allowed for the user who is assigned the role.
Each user role can contain multiple rules and each user can have multiple roles.
For example, if role1 allows access only to configuration operations, and role2 allows access only to debug operations, then users who belong to both role1 and role2 can access configuration and debug operations.
You can also limit access to specific VLANs, virtual routing and forwarding instances (VRFs), and interfaces.
The Cisco NX-OS software provides four default user roles:
•network-admin—Complete read-and-write access to the entire NX-OS device (only available in the default VDC)
•network-operator—Complete read access to the entire NX-OS device (only available in the default VDC)
•vdc-admin—Read-and-write access limited to a VDC
•vdc-operator—Read access limited to a VDC
Note You cannot change the default user roles.
Reference:
https://www.cisco.com/c/en/us/td/docs/switches/datacenter/sw/4_1/nx-os/security/configuration/guide/sec_nx-os-cfg/sec_rbac.html#wp1431408
Resources From:
1.2023 Latest Braindump2go 350-601 Exam Dumps (PDF & VCE) Free Share:
https://www.braindump2go.com/350-601.html
2.2023 Latest Braindump2go 350-601 PDF and 350-601 VCE Dumps Free Share:
https://drive.google.com/drive/folders/1M-Px6bHjOJgp4aPsLoYq-hgm90ZKxV_i?usp=sharing
Free Resources from Braindump2go,We Devoted to Helping You 100% Pass All Exams!